- KALP Foundation Appointed Dr. Joël Ruet as Executive Director
- Miller & Miller's Inaugural, Pre-1980 Sports Cards & Memorabilia Auction will be Held on January 25
- "Hunger Free Bharat" mission Launched by The Restaurant Cricket League & Adi Bodh Foundation to address Food Security
- ASH Media Co. Launches SEO Services to Drive Organic Digital Growth
- Britannia chose Nature to lead the way for its latest campaign
- IDFC FIRST Bank goes live on Direct Tax Collection System of CBDT
- XenMD Launches Comprehensive Digital Marketing Services for Healthcare Providers
- Arya Vaidya Pharmacy Expands Product Portfolio, Strengthening Its Commitment to Holistic Health and Sustainability
- RPost Launches SMART-as-a-Service with RMail Recommends™ AI
- Codilar Achieves Adobe Commerce Specialization In Apac Region
- DataVare updated MSG to VCF Converter to instantly Convert MSG Contacts to VCF Format
- Nye & Company's Jan. 22-23 Chic and Antique Auction will Feature Fine Art, Antiques and Americana
- Quest Global Announces Appointment of Rob Vatter as Executive President
- Noble Capital’s Tailored Real Estate Investment Funds Deliver Stability and Growth for Diverse Investor Needs
- Webinar Alert - HexaCorp Unveils Strategies to Untangle Data Chaos Using Hybrid Cloud
 Mail to a Friend Mail to a Friend |
|
     |
Elcomsoft Explorer for WhatsApp Use Jailbreak to Decrypts WhatsApp Cloud Backups
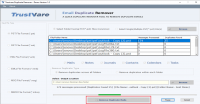
ElcomSoft Co. Ltd. updates Elcomsoft Explorer for WhatsApp, an all-in-one tool for easy acquisition and analysis of WhatsApp communication histories. Version 2.60 gains the ability to decrypt backups from Cloud Drive using device keychain. In addition, Elcomsoft Explorer for WhatsApp now supports HEIC (HEIF) images.
Elcomsoft Explorer for WhatsApp 2.60 adds the ability to decrypt WhatsApp conversations from stand-alone WhatsApp backups made on iPhone devices and retrieved from iCloud Drive. The new decryption method does not require a WhatsApp activation code.
Elcomsoft Explorer for WhatsApp 2.60 is an incremental update, adding the ability to decrypt stand-alone WhatsApp backups downloaded from iCloud Drive without receiving an activation code from WhatsApp. In previous versions, EXWA required access to the user's verified phone number (SIM card) to obtain the encryption key and decrypt the backup. The new release offers the ability to decrypt downloaded backups by using a copy of the iPhone keychain extracted from a jailbroken device.
The new decryption methods makes use of the encryption key stored on the iPhone in the keychain. While most keychain items are accessible via logical acquisition, WhatsApp targets a higher security class and can be only obtained with iOS Forensic Toolkit 4.0 via physical keychain extraction. A jailbreak is required in order to access the keychain. This key can be used to decrypt the backup in place of the code received from WhatsApp servers.
The new decryption method is optional, and offers tangible benefits over the previously used (and still available) decryption method. The expert will no longer require to obtain the security code from WhatsApp by SMS or phone call, and WhatsApp will remain active on the user's iPhone. If one does not have access to the user's SIM card and cannot receive the activation SMS, this could be the only extraction method available. The decryption key extracted from the user's keychain will work for all past and future WhatsApp backups made on that device.
Release notes:
- Added the ability to decrypt backups from Cloud Drive using device keychain
- Added support for HEIC (HEIF) images
- Added support for system messages
- Improved support for deleted messages
- Bug fixes and performance improvements
Elcomsoft Explorer for WhatsApp 2.60 is immediately available at https://www.elcomsoft.com/exwa.html
Company :-ElcomSoft Co. Ltd.
User :- Vladimir Katalov
Email :-pad@elcomsoft.com
Phone :-749-597-411
Mobile:- -
Url :- http://www.elcomsoft.com